Day 15
Set Up Two Factor Authentication
DAY 15: Set Up Two Factor Authentication
Welcome to Day 15 of my 30 day security challenge, the month long challenge I created to help you gain control of your privacy and security online. You can follow along with the security challenge via my blog at snubsie.com, where you can skip ahead or download a checklist of the challenge. Each video will also be curated into a playlist so it'll be easy to follow along from Day 1 all the way through 30 here on Youtube.
Today is all about two factor authentication. The reason why I decided to wait until halfway through the security challenge to bring up 2 factor authentication (2FA for short), along with password managers and tomorrow VPNs, is because each of these sounds like very daunting tasks and it's tough to get someone to even consider using these because they require lots of setup. BUT as with a lot of these options, the hours you spend setting up these applications will save you stress and anxiety in the future. So today let's chat 2FA.
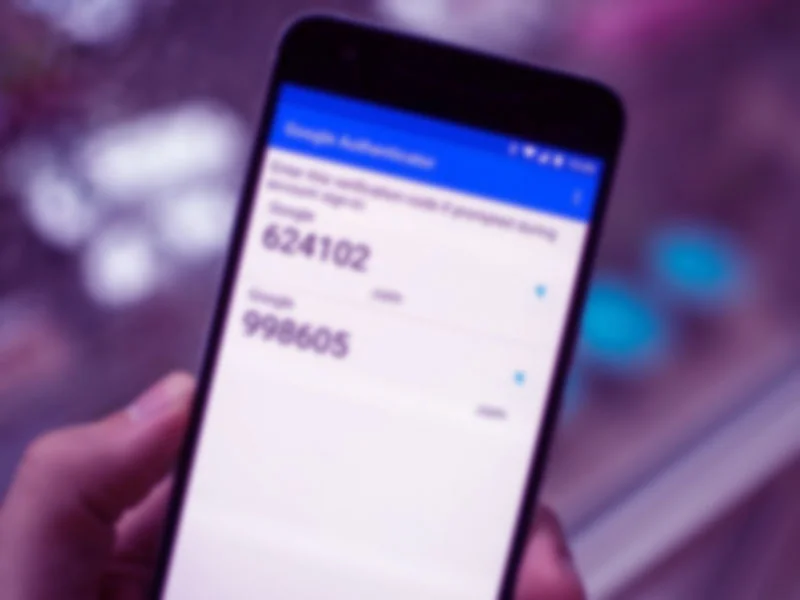
So what is two factor authentication? 2FA is a type of multi factor authentication. It consists of two of three things: knowledge (something you know), possession (something you have), and inherence (something you are). You already use this for your bank at an ATM machine. Something you have is the debit card, and something you know is your PIN - that is 2FA. Online, 2FA usually consists of something you know - your username and password, and something you have - a device that generates a code you can type in.
Typically once a website is set up to use 2FA, the process goes like this: you click login to log in to your account, type in your username and password, and click login. The website recognizes that your account has 2 Factor Authentication turned on, so it prompts you for a 6 digit passcode (the passcode can be more or less, depending on the site), then you click OK and it'll log you in. In most circumstances, the 2FA code changes every several seconds, so it never stays the same. That way if someone watches your logon over your shoulder and sees your 2FA code, they wouldn't be able to log in with the same 2FA code again - it is always changing. In the case of inherence or something you are, that could be a biometric fingerprint, voice recognition, iris scan, or more. One company that uses multifactor authentication with biometrics is Clear - a company that is showing up at airports in the US: they ask for your ID and your airplane ticket, then they scan your fingerprint in a reader and let you through security. It's basically a high tech TSA line. Anyways, 2FA.
How do you receive codes for 2FA online? You can buy a 2FA USB key, like the ones sold by Yubico at https://www.yubico.com/. You could also just use SMS, or you could download a mobile app and receive codes that way. Each of these has a drawback or two:
The drawbacks of 2FA: If you use it with a device (like a USB two factor authentication key), this requires you to walk around with an extra thing in your pocket. Most folks don't want to do that but since it's not a connected device, it can't get hacked and is less likely to get stolen. Of course, you could lose that 2FA device, then you'd be kinda screwed. If you use 2FA with your mobile phone (this is what I recommend for easiest use), your phone could get stolen or broken, then you wouldn't have access to your 2FA keys whenever they're generated in a 2FA app or SMS text. If you use an App and switch phones, you need to have some sort of backup codes to access accounts online til your new account is set up (these are usually sent to you when you first set up 2 factor on a website). Either that or you can use an app that backs up your 2FA codes for you. This might not be as secure though, since someone else could download the app and figure out your login details. SMS is the worst choice because attackers have been using social engineering to get cell phone service providers to switch SIM card phone numbers over to new phones. So even if an attack never stole your phone, they could start getting all your phone calls and texts on a new physical phone that stole your phone number. That means your 2FA SMS codes could be sent to an attacker instead of you.
Then why use 2FA if it's got drawbacks? Well, if your online account username and password was ever stolen, an attacker still couldn't get into your account without the 2FA code. The event of an attacker targeting you for your username and password AND 2FA is highly unlikely but an attacker targeting an online company to steal all the customer accounts off of it is prominent. Having that 2FA code locks them out of your account even if they got that info, so you can rest assured that your online accounts are still safe (of course, if you do find an account was compromised it's best to change that password AS SOON AS POSSIBLE).
Some options for 2FA: I already mentioned Yubico's Yubikeys for USB key 2FA, but there's also apps for your smartphone. Google Authenticator, LastPass Authenticator, Authy, and Duo are just a few options.
Download whichever one you prefer on your phone and verify your identity. I use Authy, which sends a code to my phone number to verify I actually own that number. Then it allows me to set a master password for the app and login. Once logged in, I can add all the online accounts I want. I specifically use Authy because they offer a backup solution which encrypts and backs up the 2FA tokens to Authys servers. This is NOT the most secure option, but it's convenient for my needs because I'm constantly reviewing and switching phones. Most apps don't have a backup option which is honestly more secure because you aren't putting inherent trust in a company to protect your data - it's all stored locally on your phone instead. BUT again, if you lose that phone, you could be screwed.
How do you protect yourself from getting screwed out of your accounts? Several online websites that offer 2FA security also offer backup codes when you first set up 2FA. For example, Google lets you set up 2FA then it pops up with about 10 different codes - Google asks you to Print or write down these codes because it'll be the ONLY way you can get into your account in the event that you lose your 2FA app. For any accounts that have these backup codes - write them down and store them somewhere safe. I would keep them with other crucial documents that you barely ever touch and rarely need.
Now, how do you know what websites use 2FA? Easy! Two websites have popped up to tell you which online services have 2FA and how to turn it on. https://2fa.directory/ is perfect for finding out what popular online services already have 2FA available, and also has a built in tweet function so you can tweet at any services that don't support 2FA and tell them to GET ON IT already because it's 2017 c'mon guys I'm talkin to you, Squarespace.
So go through your password manager and find each site that accepts 2 factor authentication and turn them all on, scan the QR codes with your new 2FA app, and start using those brand new 2FA codes. Yes, it is a bit more hassle to have your phone on you whenever you need to log into a new site, but it's also such a headache for attackers, they probably won't event try to steal your accounts.
You're now halfway through! Woohoo!
Day 15 is now complete! Tomorrow is all about setting up a consumer friendly VPN! But first, make sure to subscribe on youtube and hit up snubsie.com for the downloadable checklist and to skip ahead on the 30 day security challenge. Again, I'm Shannon Morse and I'll see you tomorrow for day 16!
https://authy.com/
https://play.google.com/store/apps/details?id=com.google.android.apps.authenticator2&hl=en
https://play.google.com/store/apps/details?id=com.duosecurity.duomobile&hl=en
https://duo.com/